viabl.ai User Access Control (Platform Privileges)
The privs system in the viabl.ai platform (which is separate from the deployment server) is based around individual user accounts and group roles.
These accounts and roles can then be used to apply various restrictions around the platform.
- Control access to various (global) platform features (e.g. user management)
- Control access to home screen folders
- Control access to individual knowledge bases
- Control access to Build Tools (role-based control only)
- Control access to catalog categories (on a per-KB basis) along with various KB settings
Groups, Users and Roles
- Groups within viabl.ai are used to hold users, associate deployment server(s) and setup user roles
- Users within viabl.ai are individual entities, each of which is associated with a group and is identified via a unique email address
- Roles are created on a per-group basis and group users can be assign one or more role
Global (Role) Privs
Global privs are those associated with an individual role (and hence not associated with individual KBs or folders etc).
From the launch screen, group admins have access to the Manage group roles menu option. This dialog allows the group admin to both view & edit the individual roles associated with the group. n.b. If logged in as super-admin, the per-group roles are accessed via the Manage user groups dialog instead!
| Permission ID | Permission Name | Description |
|---|---|---|
| USER_EDIT | Manage Users | This priv also grants access to managing build tool access & group role management |
| KB_CREATE | Allow knowledge base Creation | Does the role have the ability to create new knowledge bases (from the launch screen). Also restricts KB & Project import |
| KB_BUILD | Allow Project Build | If the group has the Enterprise feature enabled, does the role have the ability to build the project (from the launch screen via the blocks icon) |
| FOLDER_CREATE | Allow Folder Creation | Is this role able to create new (launch screen) folders? n.b. The user can still import a project |
| KB_DEPLOY | Allow KB Deployment (rocket) | Can this role deploy a knowledge base via the rocket icon (or the Test-Run KB menu item). n.b. This is a replacement for the previous per-user priv |
| KB_ADV_DEPLOY | Allow KB Advanced Deployment (menu item) | This controls access to the Advanced Deployment menu item. n.b. This is a replacement for the previous per-user priv |
In addition to allowing the management of roles, the dialog is also a handy place for displaying which users are assigned to each role.
Home Screen Folder Privs
Any user with owner access to a home screen folder can manage the folder's access for the group's users and roles. Privs associated with a folder are designed to control who has access to adding & removing KBs from the folder. This is un-related to their access to the individual KBs (which is assigned separately). Folder access has 4 levels...
- Owner
- A folder owner has full access over KB inclusion & removal from the folder, and can assign folder access to other users & roles
- Add & Remove
- This priv allows a user to add and remove individual KBs from the folder
- Open & Edit
- This priv implies that the user cannot add or remove KBs from the folder, but they can have access to the KBs within it (given their individual KB privs)
- None
- The user has no access to the folder (and it is hidden from them) As with individual KB access, a user's various levels of privs are combined to grant the most privileged access to the folder.
KB Access Privs
Access to individual KBs is granted by any user with "owner" to the knowledge base. Access can be granted globally, role-based or individual users. The actual level of KB access is the most privileged of all those that the individual user is included in.
e.g. If user bob@bob.com has user access set to read only, but they are a member of the "developers" role (which has read write access) and the default access is set to none then they would have read write access (because of their membership of the developers role).
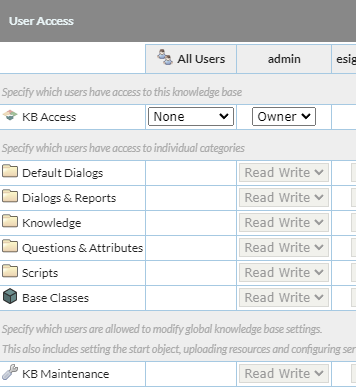
Individual KB Catalog Privs
This closely mirrors the previous privs where access to a KB's catalog categories (along with "base class" access and access to the KB Settings) can be controlled. The addition is that this can now be role based which introduces the scenario where a user can be allocated multiple access levels to individual categories. The actual access level is the least privileged access across all relevant user / role privs.
e.g. If user bob@bob.com has user access set to none for the "scripts" category, and they are a member of the "developers" role (which has read write access to "scripts") then they would have none access (because of their user access level being lower than their group access level).
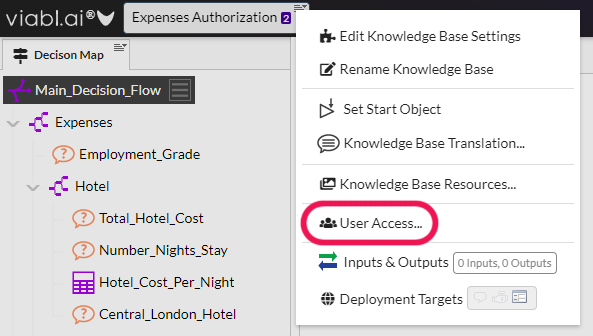
Build Tool (Role) Privs
The individual visibility of all build tools (across all KBs) can now be controlled on a per-role bases. These privs are assigned via the "Manage Build Tools" menu option on the home screen. n.b. This feature is only accessible via a user with the "EDIT_USERS" priv allocated to their role.
Roles and XpertRule Sign-In
If access to the viabl.ai platform is controlled via an XpertRule Sign-In server, the roles should be setup (but not necessarily assigned to users) as detailed above. The actual per-user roles association is managed via XSI (or the associated authentication provider). n.b. This association is (at present) a free-form text match so take care to get the spelling and capitalization correct in XSI!
n.b. If you would like to maintain the user to role associations in the viabl platform (rather than XSI), you can add the "ignore_roles": true property to the XSI section in the platform settings.json. This directs the platform to ignore the XSI associated roles and revert to the platform associated roles. e.g.
"xsi_details": {
"client_id": "xxxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx",
"client_secret": "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx",
"url": "https://xsi.acme.com",
"ignore_roles": true
}